Tech
How to Install IPVanish Firestick for Full Privacy

Do you feel like someone is watching your every online move? Want to be able to access geo-restricted material without having to leave your living room? IPVanish is the virtual private network which can be installed easily on your Firestick. You can protect your online privacy with just a few easy steps.
Online privacy and security is more important than ever in today’s world. You want to protect your personal information from prying eyes, whether you’re streaming a TV show or doing your online banking. Virtual private networks (VPN) are a great way to protect your privacy. Installing VPN on your Firestick will allow you to create a private and secure internet connection, which will keep your online activity safe from hackers, ISPs and government surveillance.
IPVanish for Firestick lets you enjoy the internet as it was intended: fast, secure, and free. You can stream by hooking up your Firestick with your laptop and enjoy streaming. You need to be protected when you watch movies, TV shows, or PPV on Firestick. Let me tell you how to be safe on Firestick with IPVanish.
How to install IPVanish Firestick using Amazon App Store?
It is easy to download apps from Amazon App Store onto your Firestick. Follow these steps to download and install IPVanish Firestick.
1. Installing IPVanish Firestick is easy. Subscribe to our Newsletter IPVanish is a VPN service.
2. After tapping Subscribe NowChoose your Product and Plan Create an account
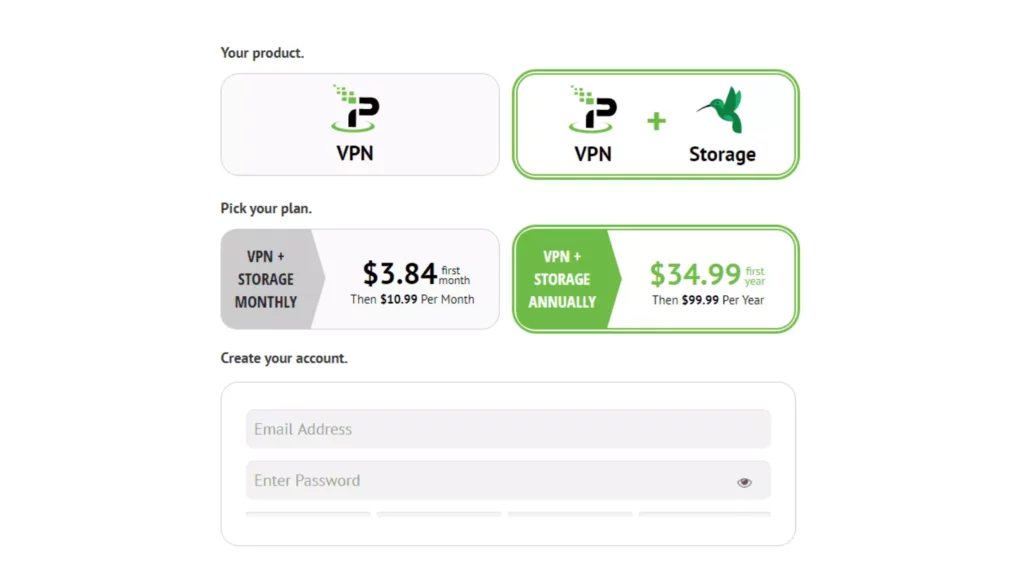
3. After selecting a Payment methodSubscribe Now.
4. Next, you’ll have to Subscribe to our newsletterYou can access this link by clicking on the email you received from IPVanish.
5. Tap on Search Engine Type IPVanish into the bar on your Firestick.
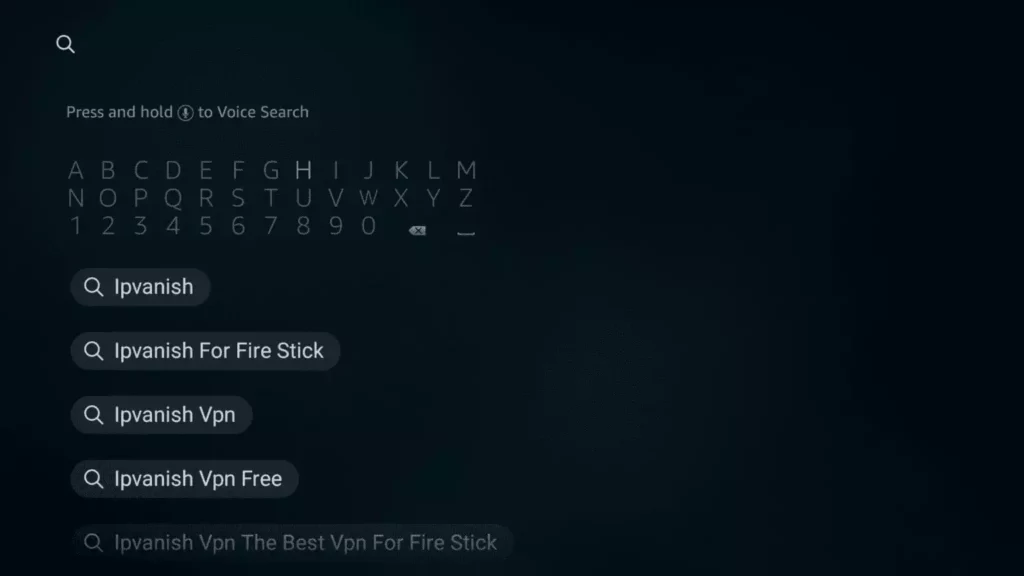
6. IPVanish is available in the Amazon App Store. Select it.
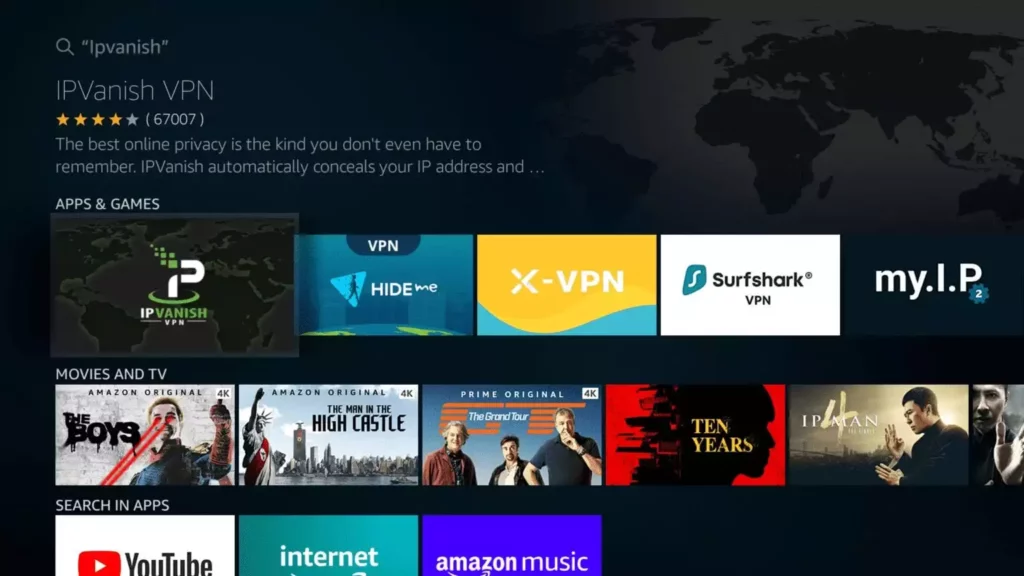
7. Next, you’ll need to press Download IPVanish for your Firestick
8. Once the download and installation is complete, go to the Apps Section on your Firestick
9. Find out launch IPVanish is required for you to use. log into it.
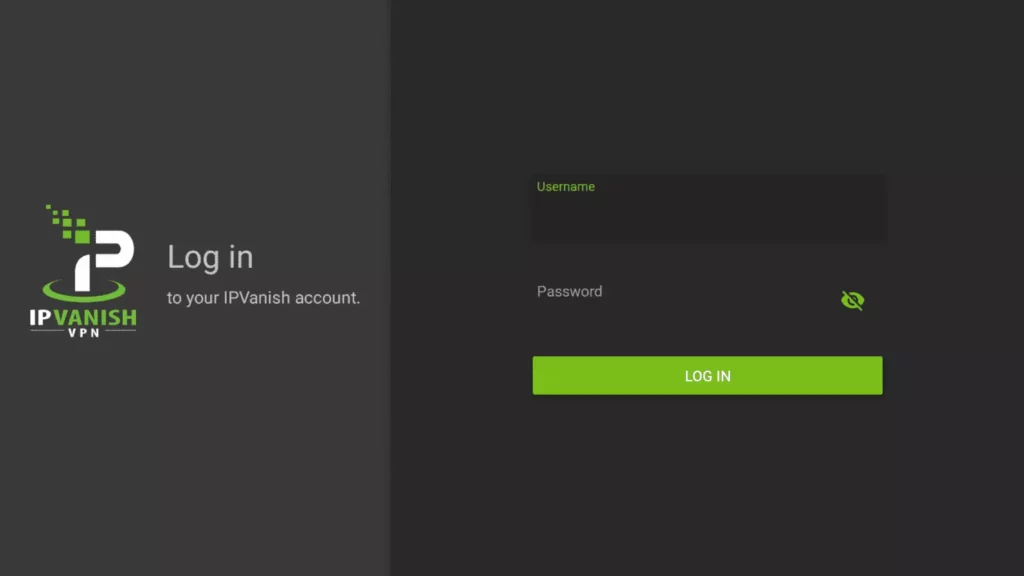
10. Next, you will need to tap on Connect with usIPVanish will list your location and IP address.
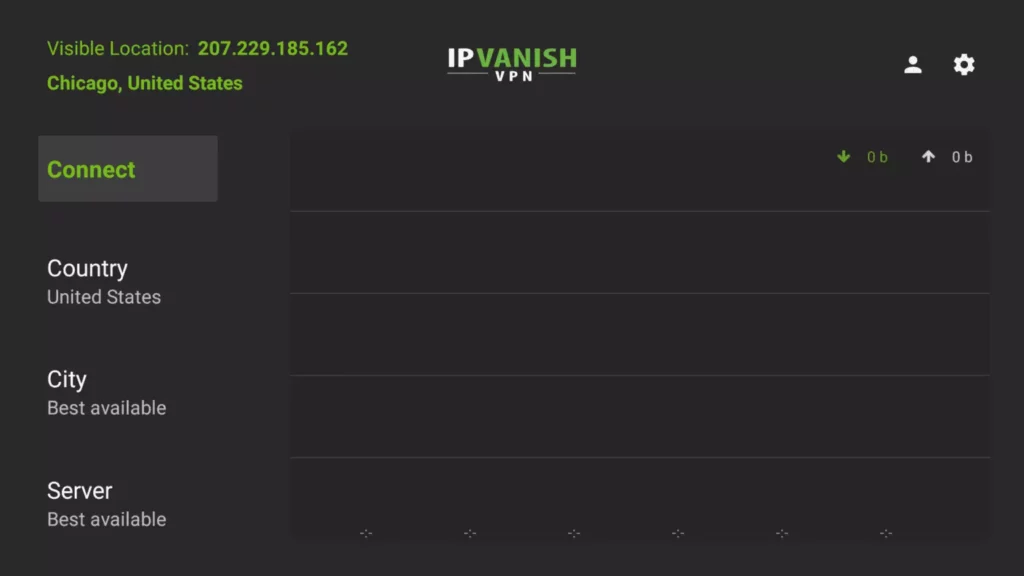
11. The IPVanish interface displays the current download and upload speed of your Fire TV after establishing the connection.
Also, read How To Install SO Player On Firestick & Set Up in 5 Minutes?
How to Install IPVanish Firestick using Downloader App?
You can also sideload IPVanish using the Downloader application. It is easy to sideload apps on Firestick. Follow these steps to install IPVanish via downloader on Firestick.
1. Find out more about My Fire TV Firestick The following are the most effective ways to reduce your risk of injury..
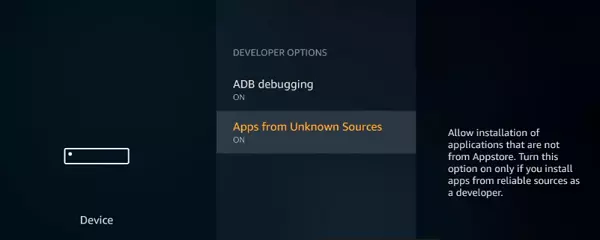
2. Turn On Apps from Unknown sources In the meantime, Developer Options.
3. Search for the Downloader app Search for Firestick in the search bar.
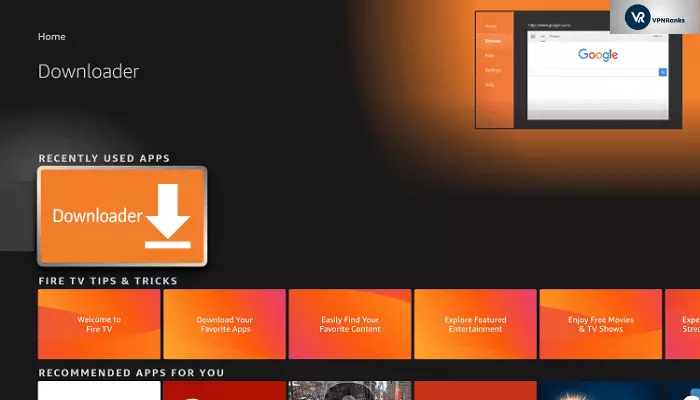
4. Download You can also find out more about the following: Install The Downloader app.
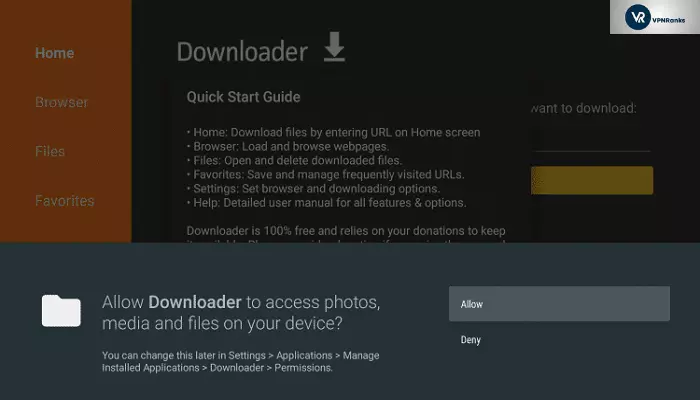
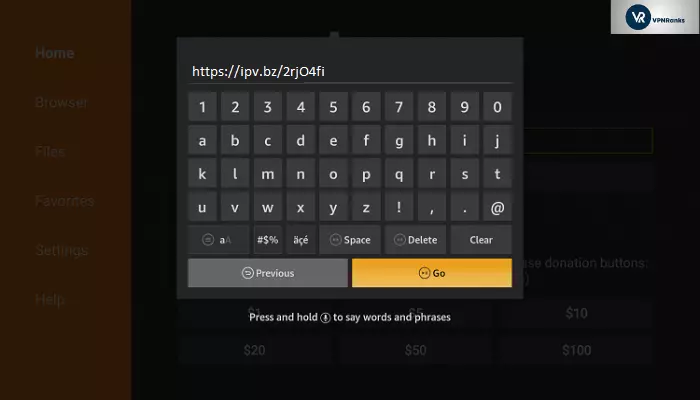
5. Enter Ipv.bz/2rjO4fi The Downloader app will display the URL in the URL box on the homescreen.
6. After the file is downloaded and installed, it can be used to Open it.
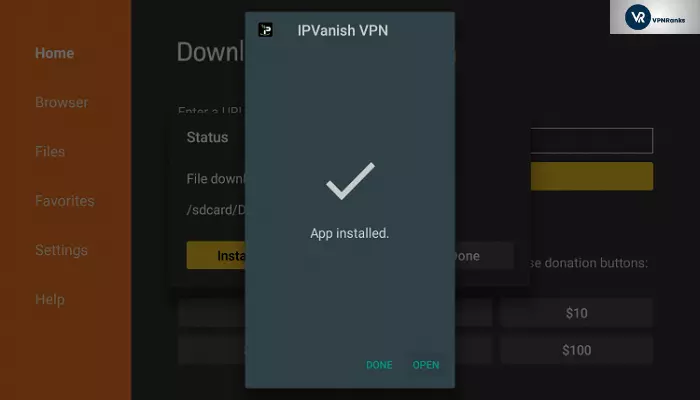
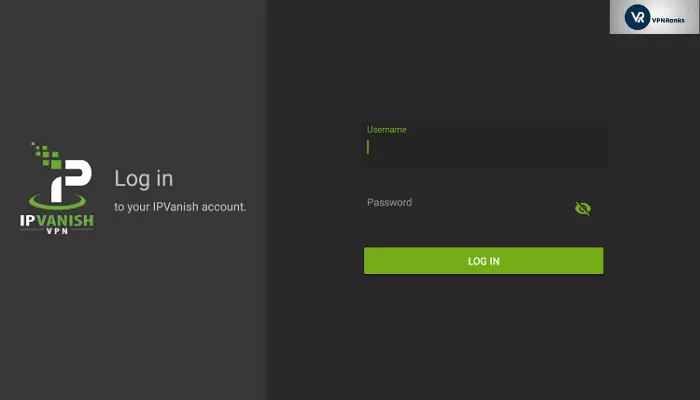
7. Launch IPVanish log into IPVanish will only work with your ID and password.
You can now use IPVanish with your Firestick.
Also, read How to Install Firestarter without Computer on Firestick?
How to Use IPVanish Firestick?
Let’s learn how to use IPVanish Firestick after you have installed it. To use IPVanish Firestick:
1. Log in Log in to your IPVanish Account by entering your login credentials at the IPVanish homepage.
2. Tap on the country you wish to connect with if you have made a choice. Country The option is located on the left side menu.
3. Select a You can also find out more about the following: Select your preferred country from the list provided.
4. Click on the button to securely stream your content. Connect with us Click the button to establish a VPN.
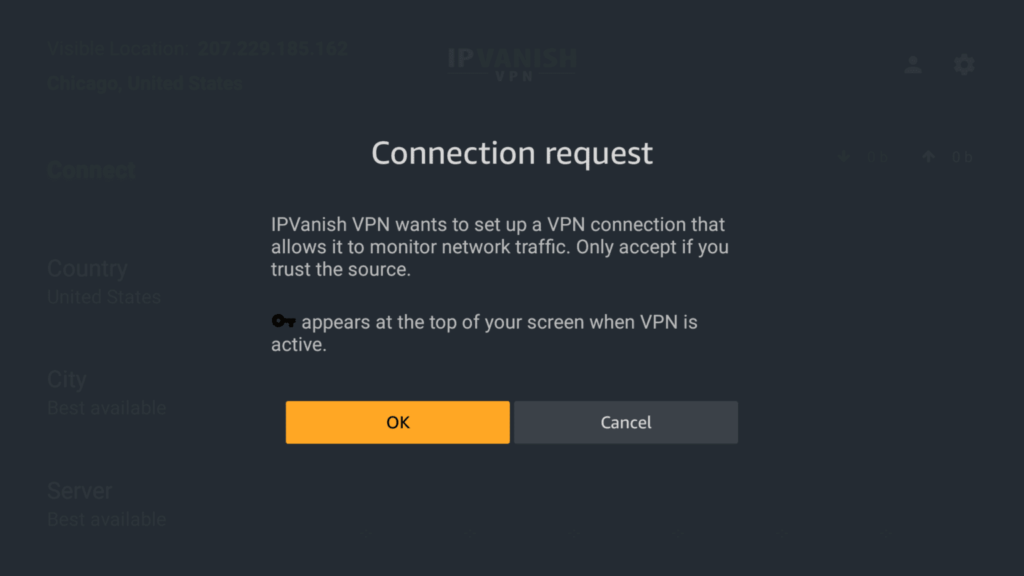
Also, read How to install Surfshark Firestick? Zero To Hero Streaming
IPVanish Features
Many people are discovering IPVanish as one of the fastest VPNs and most reliable VPNs. It’s an excellent choice for FireStick owners because of its impressive features.
1. Multiple Servers
IPVanish offers a fast and secure VPN connection. You can expect the fastest speeds with 2,200 servers in over 75 countries and 40,000+ IP addresses shared. IPVanish offers unbeatable security, giving you peace-of-mind when streaming your favorite movies and shows.
2. Split Tunneling Feature
Split tunneling allows you to control your internet traffic. You can choose which websites and applications you want to send through your ISP as well as which ones you don’t. This feature is available to FireStick users as well, so that you can control your internet privacy.
3. Unlock Geo-Restrictions

IPVanish will help you say goodbye to annoying advertisements! This VPN blocks geotargeting attempts from advertisers, meaning they can’t collect location information to send targeted ads. Plus, protocols are in place to protect your online data from marketers. IPVanish offers ad-free web browsing.
4. Enabled Security
IPVanish is serious about your online security. Their 256-bit AES is industry-standard and top-notch. IPVanish uses multiple VPN connections and protocols to offer you the best protection. Their zero-traffic-logs policy ensures your connection and activity records, as well metadata, will never be stored, so your information cannot be used against you. IPVanish will keep you safe and secure on the internet.
5. Zero Logs
IPVanish adheres to a strict “zero-logs” policy, meaning that they do not keep any records about your online activity. This is important, as it ensures your privacy will always be protected. IPVanish is a safe and secure way to protect your online activity.
6. Real Debrid Compatibility
Real Debrid allows you to access premium content via links. IPVanish supports Real Debrid. This means you can use IPVanish for secure access to Real Debrid. You will also be able to enjoy high-quality content, without any buffering. This is a great option for anyone who wants uninterrupted access to high-quality content.
7. Multiple Devices

You can connect up 10 devices at once with IPVanish. This is perfect for families with multiple devices to protect. IPVanish ensures that your devices, no matter where you are or what you do online, are secure and confidential. IPVanish can be used on your FireStick as well as your laptop, phone, tablet and more with the same account. This allows you to stay safe and secure on any device.
8. Customer Support

IPVanish offers more than just a reliable and fast VPN for FireStick. They also prioritize the needs of their customers by offering convenient features. Their customer service team is available 24/7 to answer any questions and resolve any issues in real time. The 30-day money-back warranty allows you to fully test out the service before making a purchase. You can be confident that your online experience will be in good hands with IPVanish.
Also, see How to Install Unlinked on Firestick & Bypass the App Store?
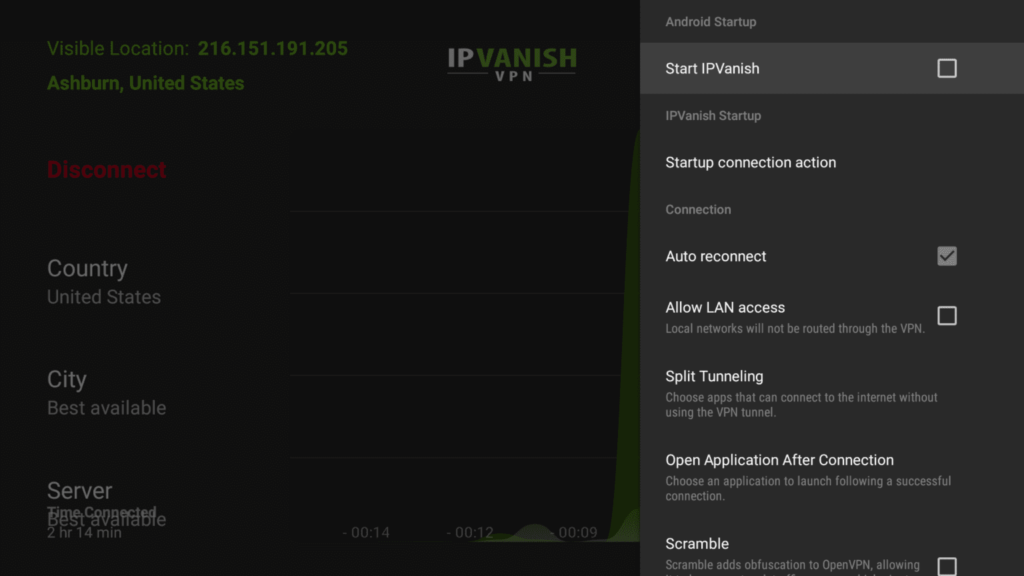
IPVanish Settings on Firetsick
The IPVanish Firestick/Fire TV app is designed to protect your online privacy. Let’s discuss some of the settings available in the IPVanish application that can help you keep your online activity safe.
Click on the white gear icon located in the upper right corner of the screen to access your IPVanish settings.
1. Start IPVanish
Start IPVanish is one of the most important features in the IPVanish settings. It launches the app automatically every time your Firestick is turned on. This is a great option for users who don’t want to have to launch the app each time they turn on their Firestick.
2. Auto Reconnect
IPVanish’s app settings include Auto Reconnect. This feature automatically reconnects your app to the VPN in the event that you lose connection. This feature is especially useful for users who are concerned about their privacy online and don’t wish to leave their devices unsecured.
3. Allow LAN Access

You’ll find a feature called “Allow LAN Access” in the settings menu. This option allows you to control whether your local network is allowed to use the VPN. When you enable it, any apps or devices connected to your local network will not be able to use the VPN. Apps like Plex Media Server and Amazon Fire TV Remote Control, for example, won’t require a VPN connection to work. Instead, they will continue to operate normally within your local networks.
4. Split Tunneling
Split Tunneling is another useful feature in the settings menu. This feature allows you divide your network connection in two parts, one for the VPN Tunnel and the other for the Internet Service Provider or local area network connection. You can select which applications use the VPN tunnel, and which use the regular ISP connection or local area network (LAN) when you activate this feature. This gives you more control over your network traffic, and allows you to use the VPN only when needed.
5. Scramble
6. Scramble is the fifth option in the Settings menu. This feature is useful when you are facing networks, firewalls or websites that block VPN. Scramble is a booster that can help you overcome these blocks. It gives you a boost to bypass any restrictions, and access the content that you need.
6. VPN Protocol

Let’s now talk about the sixth option in the settings menu: VPN protocol. This is the type of protocol that you will use to set up your VPN.
7. Protocols
IPVanish Firestick offers two protocols. OpenVPN TCP is the first protocol, which offers a reliable and highly encrypted connection. OpenVPN UDP is a second option, which provides a faster connection but with less encryption.
8. Port
Port is located just below the VPN Protocol setting. This setting allows you to choose the port number that your network traffic will use. This setting is set to 443 by default, which is the port number commonly used for HTTPS or secure web browser communication. If you don’t hear from the IPVanish Support team, it is best to leave the default setting.
9. Customer Support
Let’s now talk about two other options that you can find in the Settings menu. The first option is the Contact support, which will take you directly to IPVanish customer support and their support center.
10. Terms and Conditions
The Terms of Service is the second option, where you can review and find the most recent terms and conditions of IPVanish’s service.
Also, read How to install TeaTV on Firestick – Sip, sit and stream
Is IPVanish legal and safe?
IPVanish can be used legally in most countries. IPVanish is a VPN service that can be a valuable tool for protecting your privacy online and gaining access content that might be geographically restricted.

It is important to use a VPN responsibly and refrain from any illegal actions. It’s up the user to make sure they use any tool or technology in an ethical and lawful way. As long as you use IPVanish to achieve legitimate goals, you can be confident that the service is legal.
Also, read How To Install Set TV On Firestick To Access 550+ Channels Live?
Wrapping up
Installing IPVanish Firestick on your Firestick can enhance your online security and privacy. IPVanish will keep your internet activity private and your personal data safe from prying eyes.
Installing IPVanish onto your Firestick is well worth the effort. You can enjoy a more private and secure online experience by taking the time to protect your privacy and security online. IPVanish offers the protection you need for a safe and secure experience online, whether you are streaming movies, browsing or making sensitive transactions.
This article will show you how to install IPVanish Firestick in a few easy and simple steps.
Frequently Asked Question
1. Does IPVanish easily work on Firestick?
Absolutely. IPVanish has been designed to be easy to use and intuitive on Firestick. After installing the app, you can connect to the VPN in just a few simple clicks.
2. Can I use IPVanish on multiple devices?
You can use IPVanish simultaneously on multiple devices. You can also install IPVanish onto other devices, such as your phone, tablet, or computer.
3. Can IPVanish unblock geo-restricted content?
Yes, IPVanish can help you access geo-restricted content. IPVanish allows you to connect to a server in a foreign country. This allows you to circumvent geographical restrictions and gain access content that is not available in your area.
4. Is IPVanish a cost-effective solution?
Yes, IPVanish has a competitive subscription plan and offers flexible pricing to suit different budgets.
5. Will IPVanish slow my internet speed down?
IPVanish minimizes any speed loss. Many users have reported no noticeable speed loss while using IPVanish.
6. Does IPVanish log my internet activity?
No, IPVanish does not store any records about your internet activity. This ensures your online privacy at all times.
7. Can I cancel my IPVanish membership at any time?
You can cancel your IPVanish membership at any time, without incurring additional fees. IPVanish offers a 30-day refund guarantee so you can test the service without risk.
Tech
Ultimate Guide to Protecting Yourself from Phishing Scams

Phishing is a malicious practice used by cybercriminals to deceive individuals into revealing sensitive information such as passwords, credit card details, or social security numbers. These scammers often masquerade as trustworthy entities, such as banks, government agencies, or popular online services, in an attempt to trick unsuspecting victims. Phishing attacks usually occur through email, text messages, or fake websites designed to look legitimate.
How Phishing Scams Work?
Phishing scams rely on social engineering techniques to manipulate victims into taking action. These scams typically start with an email or message that appears to be from a reputable source, urging the recipient to click on a link or provide personal information. The link often leads to a fraudulent website that mimics the legitimate one, tricking users into entering their login credentials or other sensitive data. Once the cybercriminals gain access to this information, they can use it for various malicious purposes, including identity theft, financial fraud, or unauthorized access to personal accounts.
Types of Phishing Scams
Phishing scams come in various forms, each with its objective and method of deception. Some common types of phishing scams include:
Email phishing: This is the most common form of phishing, where scammers send fraudulent emails disguised as legitimate organizations. These emails often contain urgent requests for personal information or ask users to click on malicious links.
Spear phishing: Unlike regular phishing attacks, spear phishing targets specific individuals or organizations. The scammers gather information about their targets to personalize the attack and make it more convincing.
Whaling: Whaling attacks specifically target high-profile individuals, such as CEOs or executives, to gain access to sensitive corporate information or financial assets.
Smishing: Smishing, or SMS phishing, involves sending fraudulent text messages that appear to be from trusted sources. These messages often contain links or requests for personal information.
Vishing: Vishing, or voice phishing, relies on phone calls to deceive victims into revealing sensitive information. Scammers may pose as bank representatives, government officials, or technical support personnel to gain the victim’s trust.
Signs of a Phishing Attack
Here are some common indicators that can help you identify a phishing attempt:
Sender’s email address: Pay close attention to the email address of the sender. Phishing emails often use domain names that are slightly different from the legitimate ones, such as “g00gle.com” instead of “google.com.”
Urgency or fear tactics: Phishing emails often create a sense of urgency or fear to prompt immediate action.
Poor grammar and spelling: Phishing emails often contain grammatical errors, spelling mistakes, or awkward phrasing.
Unsolicited requests for personal information: Legitimate organizations rarely ask for personal information via email or messages. Be skeptical of any unsolicited requests for passwords, credit card numbers, or social security numbers.
Suspicious URLs: Hover your mouse over any links in the email without clicking on them. If the link does not match the displayed text or leads to a suspicious website, it’s likely a phishing attempt.
Tips to Avoid Phishing Scams
Protecting yourself from phishing scams requires a combination of vigilance and awareness. Here are some tips to help you identify and avoid phishing scams:
Think before you click: Be cautious of any links or attachments in emails or messages, especially if they’re unsolicited or seem suspicious. Verify the legitimacy of the sender and the content before clicking on anything.
Double-check the sender: Verify the email address of the sender and look for any signs of it being a spoofed or fake address.
Be skeptical of urgent requests: Phishing emails often create a sense of urgency to manipulate victims. Take a step back and evaluate the situation critically
Don’t share personal information: Be cautious of providing personal information, such as passwords or social security numbers, via email or messages. Legitimate organizations have secure channels for such requests.
Keep your devices and software updated: Regularly update your operating system, web browsers, and security software to ensure you have the latest protections against phishing attacks.
Educate yourself: Stay informed about the latest phishing techniques and scams.
How to Protect Yourself from Phishing Scams?
Protecting yourself from phishing scams requires a proactive approach and the adoption of best practices for online security. Here are some effective measures to safeguard your personal information:
Use strong and unique passwords: Create complex passwords that include a combination of letters, numbers, and special characters. Avoid reusing passwords across multiple accounts to minimize the risk of compromise.
Enable two-factor authentication: Two-factor authentication adds an extra layer of security by requiring a secondary verification method, such as a fingerprint or a one-time code sent to your phone, when logging into an account.
Be cautious of sharing personal information online: Be mindful of the information you share on social media platforms and other online platforms. Cybercriminals can use this information to craft personalized phishing attacks.
Regularly update your antivirus software: Keep your antivirus software up to date to protect against the latest phishing threats. Antivirus software can help detect and block malicious websites and attachments.
Encrypt your sensitive data: Use encryption tools to protect your sensitive data, such as financial information or personal documents. Encryption ensures that even if your data is intercepted, it remains unreadable to unauthorized individuals.
Backup your data: Regularly backup your important files and documents to an external hard drive or cloud storage. In the event of a successful phishing attack, having backups ensures you can recover your data without paying a ransom.
Best Practices for Secure Online Behavior
In addition to protecting yourself from phishing scams, practicing secure online behavior can significantly reduce your risk of falling victim to cybercriminals. Here are some best practices to follow:
Keep your software updated: Regularly update your operating system, web browsers, and other software to ensure you have the latest security patches and bug fixes.
Use a firewall: Enable a firewall on your computer or network to monitor and block unauthorized access attempts.
Use a secure network: Avoid accessing sensitive information or conducting financial transactions while connected to public Wi-Fi networks. Use a virtual private network (VPN) when accessing the internet on untrusted networks.
Beware of suspicious downloads: Be cautious when downloading files from the internet, especially from unknown sources. Malicious software can often be disguised as legitimate files.
Regularly check your accounts: Periodically review your bank statements, credit card statements, and other financial accounts for any unauthorized transactions. Report any suspicious activity immediately.
Educate yourself and your family: Teach your family members, especially children, about the risks of phishing scams and the importance of online security. Encourage them to follow best practices and report any suspicious activity.
Enhance your Online Security
Several tools and technologies can significantly enhance your online security and protect you from phishing scams. Here are some recommended options:
Password managers: Password managers securely store and generate strong passwords for your various online accounts. They can also help detect and warn you of potential phishing websites.
Email filters: Enable strong spam filters on your email accounts to automatically detect and filter out phishing and spam emails.
Web browser security extensions: Install browser extensions that provide additional security features, such as anti-phishing protection and website reputation ratings.
Antivirus and anti-malware software: Invest in reputable antivirus and anti-malware software that can detect and block phishing attacks, malicious websites, and infected files.
Virtual private network (VPN): A VPN encrypts your internet connection, ensuring your online activities are secure and private. It can also help protect against phishing attempts on unsecured networks.
Final Thoughts!
Phishing scams continue to pose a significant threat to individuals and organizations alike. By understanding how these scams work, being vigilant for signs of phishing attempts, and adopting best practices for online security, you can protect yourself from falling victim to these cybercriminals. Remember to stay informed, educate yourself and others, and utilize the available tools and technologies to enhance your online security. By staying one step ahead of cybercriminals, you can safeguard your personal information and enjoy a safer online experience.
Tech
OpenAI Releases GPT 3.5 Turbo Instruct

OpenAI, a leading artificial intelligence (AI) research laboratory, has recently released its latest model, GPT-3.5 Turbo Instruct. This groundbreaking development has the potential to revolutionize the way we interact with AI systems and unlock new possibilities in various industries. In this article, we will delve into the capabilities of GPT-3.5 Turbo Instruct, understand how it differs from previous versions, explore its use cases, discuss the benefits and limitations, provide guidance on getting started, showcase successful implementations, touch upon the future of AI, and address ethical considerations.
Understanding Turbo Instruct GPT-3.5
Turbo Instruct GPT-3.5 is an advanced language model developed by OpenAI. It leverages the power of deep learning to generate human-like text based on the given prompts and instructions. This model boasts an impressive 175 billion parameters, enabling it to comprehend and generate highly sophisticated responses. With GPT-3.5 Turbo Instruct, users can communicate with AI systems more naturally and intuitively, making it a game-changer for a wide range of applications. The capabilities of GPT-3.5 Turbo Instruct extend beyond simple text completion. It can understand and follow detailed instructions, assisting users in complex tasks such as coding, writing, translation, and more. Whether it’s generating code snippets, drafting emails, or even creating conversational agents, GPT-3.5 Turbo Instruct can provide valuable assistance by generating high-quality content that aligns with user instructions.
How GPT-3.5 Turbo Instruct Different?
GPT-3.5 Turbo Instruct builds upon the successes of its predecessors while introducing notable advancements. One key difference is its enhanced ability to understand and execute instructions. GPT-3.5 Turbo Instruct has been fine-tuned to better comprehend and follow user instructions, resulting in more accurate and contextually appropriate outputs. Another improvement in GPT-3.5 Turbo Instruct is its increased efficiency. Despite the significant increase in parameters, OpenAI has optimized the model to provide faster response times, reducing the waiting period for users. This improvement is crucial for real-time applications where quick responses are essential. Additionally, GPT-3.5 Turbo Instruct exhibits an impressive level of versatility.
Use Cases for GPT-3.5 Turbo Instruct
The applications of GPT-3.5 Turbo Instruct are vast and varied, spanning multiple industries. One prominent use case is in the field of software development. Developers can harness the power of GPT-3.5 Turbo Instruct to generate code snippets, debug programs, or even build entire applications. The model’s ability to understand and follow instructions makes it a valuable asset for developers seeking efficient and reliable coding assistance. Another area where GPT-3.5 Turbo Instruct shines is in the realm of content creation.
Whether it’s writing blog articles, drafting marketing copy, or generating social media posts, the model can provide valuable assistance in generating high-quality content. Content creators can leverage GPT-3.5 Turbo Instruct to overcome writer’s block, generate creative ideas, or simply streamline their content creation process. Furthermore, GPT-3.5 Turbo Instruct can be utilized in the customer service industry. It can generate responses to customer inquiries, providing quick and accurate solutions. This can significantly enhance the efficiency of customer support teams and improve overall customer satisfaction. These are just a few examples of the countless possibilities that GPT-3.5 Turbo Instruct offers. Its versatility and ability to adapt to various domains make it a valuable tool for industries across the board.
Getting Started with GPT-3.5 Turbo Instruct
Getting started with GPT-3.5 Turbo Instruct is a straightforward process. OpenAI provides comprehensive documentation and resources to assist users in understanding and harnessing the model’s capabilities. The OpenAI API allows developers to integrate GPT-3.5 Turbo Instruct into their applications seamlessly. To begin, users need to sign up for the OpenAI platform and familiarize themselves with the API documentation. The documentation provides detailed instructions on how to set up the API, make requests, and handle responses.
OpenAI also offers various code examples and tutorials to help users get started quickly. Once the API is set up, users can experiment with different prompts and instructions to observe the model’s outputs. It is recommended to start with smaller, well-defined tasks to gain familiarity with the model and gradually explore more complex use cases. OpenAI’s developer community is vibrant and supportive, offering valuable insights, tips, and best practices. Engaging with the community can provide additional guidance and inspiration for utilizing GPT-3.5 Turbo Instruct effectively. By following the provided resources, users can embark on their journey with GPT-3.5 Turbo Instruct confidently and unlock its vast potential.
Examples of Successful Implementations of GPT-3.5 Turbo Instruct
GPT-3.5 Turbo Instruct has already proven its worth through successful implementations across various domains. One notable example is in the field of education. The model has been utilized to generate interactive and dynamic learning materials, providing students with personalized and engaging content. By tailoring the generated content to individual learning styles and preferences, GPT-3.5 Turbo Instruct enhances the learning experience and promotes knowledge retention.
Another application of GPT-3.5 Turbo Instruct is in the realm of chatbots and virtual assistants. By leveraging the model’s language generation capabilities, developers have created conversational agents that can hold more natural and human-like conversations. These chatbots can assist users in tasks such as making reservations, answering inquiries, and providing recommendations, offering a seamless and efficient user experience.
Furthermore, GPT-3.5 Turbo Instruct has been employed in the healthcare industry to generate medical reports and assist in diagnostics. By understanding medical instructions and generating accurate reports, the model reduces the burden on healthcare professionals and enhances the speed and accuracy of diagnoses. These examples highlight the versatility and potential of GPT-3.5 Turbo Instruct in transforming various industries. As the technology continues to evolve, we can expect to witness even more innovative implementations in the future.
Exploring the Future of AI and GPT-3.5 Turbo Instruct
GPT-3.5 Turbo Instruct represents a significant milestone in the advancement of AI, but it is just the beginning. As technology continues to evolve, we can expect even more powerful and sophisticated models to emerge. The future of AI holds the promise of even more seamless integration with our daily lives, enabling us to accomplish tasks more efficiently and effortlessly. With GPT-3.5 Turbo Instruct, OpenAI has showcased the incredible potential of AI models that can understand and execute complex instructions. This opens up a world of possibilities for applications in industries such as education, healthcare, customer service, and content creation. As researchers and developers continue to push the boundaries of AI, we can anticipate further breakthroughs that will reshape the way we interact with technology.
Ethical Considerations when Using GPT-3.5 Turbo Instruct As with any powerful technology, ethical considerations are crucial when utilizing GPT-3.5 Turbo Instruct. It is essential to ensure responsible and ethical use to avoid potential pitfalls and challenges. One primary concern is the potential for biased or unethical content generation. GPT-3.5 Turbo Instruct relies on the data it has been trained on, which can introduce biases present in the training data. It is important to carefully review and mitigate any biases that may arise in the generated content, especially in sensitive domains.
Another ethical consideration is the responsible handling of user data. As users interact with GPT-3.5 Turbo Instruct, data is collected and processed. It is crucial to prioritize user privacy and data security, ensuring that user information is handled by relevant laws and regulations. OpenAI has been proactive in addressing these ethical concerns and has implemented safety mitigations to prevent misuse of the technology. However, it is the responsibility of users and developers to exercise caution and uphold ethical standards when working with GPT-3.5 Turbo Instruct.
Final Thoughts
OpenAI’s release of GPT-3.5 Turbo Instruct marks a significant milestone in the field of AI. The model’s advanced language generation capabilities and enhanced ability to understand instructions open up a world of possibilities for various industries. From software development to content creation, customer service to education, GPT-3.5 Turbo Instruct offers versatile and powerful solutions. As with any transformative technology, it is important to recognize the benefits and limitations of GPT-3.5 Turbo Instruct.
By understanding its capabilities and ethical considerations, users can leverage the model responsibly and effectively. The future of AI is filled with exciting possibilities, and GPT-3.5 Turbo Instruct is just the tip of the iceberg. As researchers and developers continue to push the boundaries, we can anticipate even more advanced and sophisticated AI models that will shape the way we interact with technology. It is an exciting time for AI, and GPT-3.5 Turbo Instruct is leading the way towards a more intelligent and intuitive future.
Tech
A Closer Look at Apple’s iPhone 15 and iPhone 15 Plus

When it comes to smartphones, Apple has always been at the forefront of innovation. The iPhone series has consistently set the benchmark for what a premium smartphone should be. With the recent release of the iPhone 15 and iPhone 15 Plus, Apple continues to push the boundaries of technology and design. In this article, we will take a closer look at these two new devices and explore their key features, specifications, and more.
Features and Specifications
The iPhone 15 Plus takes the already impressive features of the iPhone 15 to the next level. One of the standout features of the iPhone 15 Plus is its larger display. It comes with a massive 6.7-inch Super Retina XDR OLED display, offering an immersive viewing experience. The display also supports ProMotion technology, which provides a smooth scrolling experience and adaptive refresh rates.
Under the hood, the iPhone 15 Plus is powered by the same A15 Bionic chip found in the iPhone 15. This ensures that the device can handle even the most demanding tasks effortlessly. Whether you’re editing videos, playing graphics-intensive games, or multitasking, the iPhone 15 Plus delivers exceptional performance.
The camera system on the iPhone 15 Plus is another area where it shines. It features a triple-camera setup with wide, ultra-wide, and telephoto lenses. This allows for greater versatility when it comes to photography, with the ability to capture stunning wide-angle shots or zoom in for detailed close-ups. The enhanced Night mode on the iPhone 15 Plus further improves low-light photography, capturing more detail and reducing noise.
Design and Display
Apple has always been synonymous with sleek and elegant design, and the iPhone 15 and iPhone 15 Plus are no exception. Both devices feature a glass front and back, with a stainless steel frame. The glass back allows for wireless charging, making it convenient for users who prefer to charge their devices wirelessly.
The display on both devices is truly stunning. The iPhone 15 features a 6.1-inch Super Retina XDR OLED display, while the iPhone 15 Plus comes with a larger 6.7-inch display. Both displays offer vibrant colors, deep blacks, and excellent contrast, making everything on the screen look incredibly sharp and vivid.
Camera Capabilities
Apple has always been known for its exceptional camera capabilities, and the iPhone 15 and iPhone 15 Plus are no exception. Both devices feature a dual-camera setup with wide and ultra-wide lenses, allowing users to capture a wide range of shots. The 12-megapixel sensors, combined with the new sensor-shift optical image stabilization, ensure that photos are sharp and steady, even in low-light conditions.
The Night mode on both devices has also been improved, allowing for better low-light photography. Whether you’re capturing a night skyline or a dimly lit room, the iPhone 15 and iPhone 15 Plus can produce stunning photos with enhanced detail and reduced noise.
Performance and Battery life
When it comes to performance, the iPhone 15 and iPhone 15 Plus are in a league of their own. Both devices are powered by the A15 Bionic chip, which delivers industry-leading performance and efficiency. Whether you’re running multiple apps simultaneously, editing videos, or playing graphics-intensive games, the iPhone 15 and iPhone 15 Plus can handle it all with ease.
Battery life is another area where these devices excel. The iPhone 15 features a larger battery compared to its predecessors, providing all-day battery life. The iPhone 15 Plus, with its larger size, offers an even longer battery life, ensuring that you can go through the day without worrying about running out of power.
Software and Operating System
The iPhone 15 and iPhone 15 Plus come with the latest version of iOS, Apple’s operating system. iOS offers a seamless and intuitive user experience, with a host of features and enhancements. From the redesigned Control Center to the improved Siri, iOS on the iPhone 15 and iPhone 15 Plus takes user interaction to a whole new level.
Additionally, both devices support the latest software updates from Apple, ensuring that you have access to the latest features and security enhancements. With regular software updates, you can rest assured that your device will continue to perform optimally and remain secure.
Pricing and Availability
The iPhone 15 and iPhone 15 Plus are available in various storage capacities to suit different user needs. The pricing of these devices varies depending on the storage capacity and the region in which you are purchasing them. It is recommended to check Apple’s official website or visit an authorized retailer for the most up-to-date pricing information.
As for availability, Apple typically releases its new devices in a phased manner, with different regions getting access to the devices at different times. It is advisable to check Apple’s website or contact your local Apple store for information on availability in your region.
Final Thoughts
The iPhone 15 and iPhone 15 Plus are a testament to Apple’s commitment to innovation and excellence. With their impressive features, stunning displays, powerful performance, and exceptional camera capabilities, these devices are sure to impress even the most discerning users.
Whether you’re a professional photographer looking for a portable camera solution or a power user who needs a device that can handle demanding tasks, the iPhone 15 and iPhone 15 Plus deliver on all fronts. With their sleek design, intuitive software, and long battery life, they are truly the epitome of a premium smartphone.
If you’re in the market for a new smartphone that offers the best of what technology has to offer, look no further than the iPhone 15 and iPhone 15 Plus. Visit Apple’s official website or your local Apple store to learn more about these incredible devices and make your purchase today.
-

 Sports7 days ago
Sports7 days agoOfficial: Juventus announces sixth purchase
-

 Health & Society7 days ago
Health & Society7 days agoThe intoxicated society
-

 Politics5 days ago
Politics5 days agoThe Russian patriarch to Putin: You are the first truly Orthodox president
-

 Sports6 days ago
Sports6 days agoBeautiful Juve: Vlahovic and youth rout Verona. Thiago Motta first
-

 Sports6 days ago
Sports6 days agoJuventus, Vlahovic: “Now we play a different game.”
-

 Politics4 days ago
Politics4 days agoEU Intensifies Pressure: Six-Month Extension of Russia Sanctions
-

 Health & Society3 days ago
Health & Society3 days ago7 Superfoods That Will Boost Your Fitness Results
-

 EU & the World5 days ago
EU & the World5 days agoBrittany Cartwright Files for Divorce From Jax Taylor After 5 Years of Marriage









